A particular type of crime is dramatically on the rise, soaring 300% over the last few years. But it's not something you'll see on the latest Netflix heist drama or even in the shadiest dark alleys. We're talking about cybercrime, and anyone who uses the internet is at risk of becoming a victim. According to business technology consultant Judge, the surge in cybercrime coincided with the onset of the COVID-19 pandemic, and 95% of it is attributed to human error. It's easy to draw the conclusion that the shift to remote work was also in some way responsible, likely due to companies not being prepared to handle remote data security.
But we live and learn, and a new awareness is growing around cybersecurity and remote teams. Your remote workers do not have to be victims (nor does your business). The best way to prevent security breaches and cybercrime? Practice cyber-defense. Here, we'll take a look at the biggest risks to your remote team and some data security best practices you can employ to keep your employees, your data, and your brand safe.
Security Risks for Remote Teams
Security breaches can cost companies millions or even billions of dollars, depending on how quickly the threat is found and neutralized. Prevention is critical, and to do that, we need to understand the risks.

Phishing Scams
Phishing usually happens via email, with cybercriminals posing as reputable companies and brands that are familiar to the recipient. Phishing scams are much more sophisticated now and authentic enough to fool even savvy web users. In this way, hackers can get credit card numbers, passwords, and personal information handed to them voluntarily.
Ransomware
Ransomware is a form of malware that is on the rise. In this scheme, the ransomware is installed on a company's servers or computer system, which it then completely locks until a certain amount of money has been paid. Healthcare networks are especially vulnerable to ransomware, but it can happen to any business.
BYOD
This is a major problem for remote teams. BYOD (bring your own device) policies have led to greater risks for teams who do not supply hardware and equipment to their teams. As many workers use their personal devices, they become more susceptible to cyberattacks.
Weak Passwords
This is another consequence of employees using their own devices and accessing cloud-based apps and programs from them. Many employees select passwords that are easy to remember and/or reuse older passwords. These practices make them — and your business — more vulnerable.
Video Attacks
Another type of hacking that's risen with the shift to remote work is cyberattacks on video calls. With remote teams now relying on video conferencing platforms, hackers have discovered a new opportunity to eavesdrop and infiltrate, gaining access to important and often private information.
Data Security Best Practices for Remote Teams
So, how can you minimize the risk of cybercrime for your remote team? Nothing, of course, is foolproof, but you can ensure your team members and your data are as safe as possible by implementing these best practices:
Use a VPN
Firewalls have long been the first line of defense in cybersecurity, but they are not infallible. Firewalls can be breached and often are (more often than you'd care to think). If possible, consider getting a VPN (virtual private network) for your team. This makes it nearly impossible for anyone outside the network to gain access and is a great solution for hybrid teams, as it grants the same permissions for both on-site and off-site employees.
Provide Dedicated Devices
The way to mitigate risks around BYOD is for you to provide those devices. If it's financially realistic for your team, it's one of the best ways to reduce risk. It can have other benefits, too, like improving employee productivity and resource management. These are all reasons that, at FPS, we provide FTEs with a new MacBook Air upon their hiring and give them the option to buy it outright down the road.
Conduct Security Training at Onboarding
Training and education are so important to cyber and data security, and if it isn't already, it needs to be part of your onboarding process for new hires. But make sure it isn't just available for new employees — you'll want to refresh the entire team on security protocols at regular intervals. Typically, that's once a year at minimum.
Employ Password Management
As mentioned above, weak passwords can degrade your security to dangerous levels. Just like a few weak links in a chain-link fence can create a vulnerability that brings down the entire structure, a couple of bad passwords can do the same to your data security. Use a password manager to ensure the entire team is protected and secure, no matter which platforms they're logging into. At FPS, we use 1Password, which is easy to use and is supported across all our platforms.
Use Multi-Factor Authentication
MFA is a great way to boost security for password-protected apps and platforms. Even with a password manager, there may be certain circumstances or certain softwares that have greater sensitivity and require additional security. MFA requires at least two authenticating factors, and sometimes more, whether it's a code, a pin, or a personal question.
Implement Data Encryption
For teams that manage or have access to extremely sensitive personal data, you are wise to consider using a data encryption tool. This could be an external tool, or you could instead choose a cloud-based storage system that has data encryption built in.
Upgrade Tools to Pro Level
When it comes to the tools you use, especially for remote communication, paid is always better. Free trials or freemiums can put your team members at risk. With paid or professional tiers, you usually have some form of heightened security built in.
Put a Response Plan in Place
Prevention is key, but it's not a guarantee that you'll never fall victim to a cyberattack. Whether it happens or not, you can always be prepared. Build a plan before the worst-case scenario, so you'll know exactly what steps you need to take.
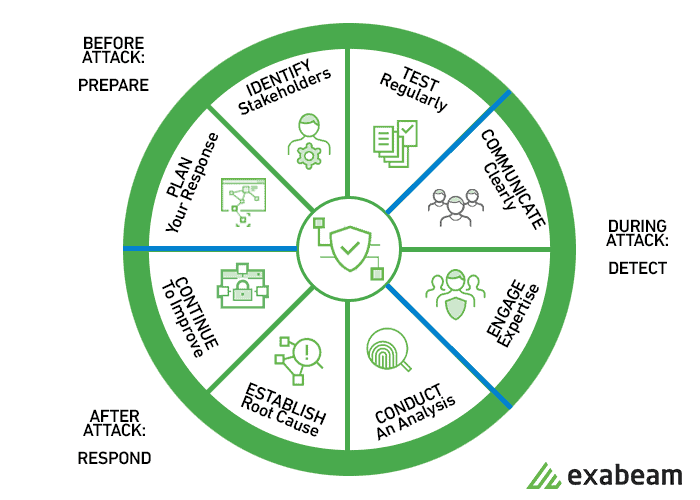
Early phases should be identifying the who and the how. In the midst of an attack, your priorities are to take out the threat with expert support and keep communications open. Afterward, you'll want to dive into the analysis, so you can understand why it happened and how to keep it from reoccurring.
Keep Your Remote Team Safe and Secure
Keep all your sensitive data safe, too. It may seem like an overwhelming task, but if you start with a solid plan and then implement these best practices, you'll reduce your risk and protect your data and your team members, no matter where, when, or how they work.